how to download wifi on your laptop
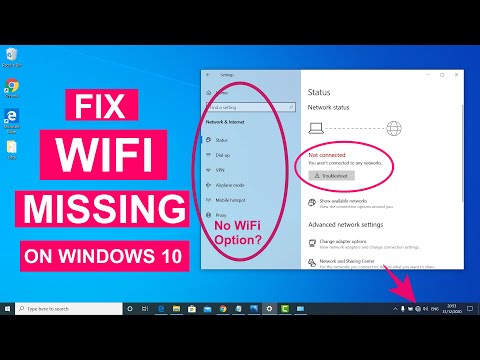
Title: Fix WiFi Not Showing in Settings On Windows 10 Fix Missing WiFi 2025
Channel: Sandeep Singh
Fix WiFi Not Showing in Settings On Windows 10 Fix Missing WiFi 2025 by Sandeep Singh
how to download wifi in laptop, how to download wifi driver in laptop, how to download wifi software in laptop, how to download wifi hotspot in laptop, how to download internet explorer on my laptop, how to download internet in laptop, how to download internet explorer in laptop, how to download wifi driver for lenovo laptop, how to download wifi driver for hp laptop, how to download wifi driver for dell laptop
Steal Your Neighbor's Wi-Fi: The Secret Laptop Download Trick!
Forget the Hustle: Unlocking Free Wi-Fi Adventures
We've all been there. The internet connection sputters. The urge for immediate connection hits hard. It's a modern-day crisis! Instead of panicking, let's explore a different solution. We can uncover some simple tactics. They may help you secure free Wi-Fi access. But, proceed with caution.
The Wi-Fi Whisperer's Toolkit: A Discreet Approach
First, we must clarify something important. We're not talking about blatant theft. We’re talking about the ethical exploration of open networks. Think of it as a digital treasure hunt. You are searching for unlocked gateways to the online world. Always respect boundaries. Do not attempt unauthorized access.
So, what tools does a savvy explorer require? First, we need a laptop. It's the primary tool. Also, grab a good Wi-Fi analyzer tool. Some are available for free. Others offer premium features. Next, a strong dose of curiosity helps tremendously. Finally, remember common sense.
Decoding the Digital Landscape: Seeing the Invisible Waves
The air around us teems with Wi-Fi signals. Most often, we can’t see them. But, with the right tools, we can perceive these unseen waves. Wi-Fi analyzers act as your digital radar. They display nearby networks. They show signal strength and security settings. They provide invaluable insights.
Consider the signal strength. A powerful signal means a more consistent connection. Weak signals mean a frustrating experience. Also, examine the security settings. Open networks, as you might imagine, are unsecured. They present the easiest entry point. But, consider the security risks. Networks using encryption require a password.
The Password Predicament: Cracking the Code? (Proceed with Caution!)
Bypassing security measures is usually illegal. Thus, we will steer clear of discussing any illegal actions. Instead, we might explore some open networks. They offer a risk-free gateway. You might discover a friendly neighbor with an open network. Now, it's all about ethical behavior.
We can analyze the network's name (SSID). Do you see any clue? Sometimes, neighbors leave clues. These might include the network owner’s name. It's often worth a try to politely ask for access. Most people are happy to help. Always be respectful. This approach is the ethical path. It's also the friendliest.
Beyond the Basics: Smart Tactics for Wi-Fi Warriors
Beyond network analysis, you can also use a few tricks. We can also consider public Wi-Fi hotspots. Libraries, coffee shops, and parks offer free access. They provide a safe and legal alternative. But, always protect your data. Use a VPN when on public networks.
Also, consider extending your range. Sometimes, a simple trick can help. Place your laptop near a window facing the signal. It can improve connectivity. Moreover, you might explore a Wi-Fi extender. These devices amplify the existing signal. It creates better coverage.
Ethical Considerations: Navigating the Digital Frontier
Let's be clear. Unauthorized Wi-Fi access poses security risks. It can expose your data. Always respect your neighbor's networks. Furthermore, understand the local laws. They vary by location. Thus, be responsible. Always prioritize ethical behavior.
Now, remember to use common sense. Avoid any activity that's shady. If in doubt, don't do it. Instead, opt for a public hotspot. Moreover, you might consider your own internet plan. It assures safe and reliable access. Ultimately, responsible behavior is key.
Conclusion: Staying Connected Responsibly
Securing free Wi-Fi is a fascinating journey. The pursuit offers some opportunities. We can learn about network technology. But, your focus should always be on ethics. Thus, play it safe. The rewards of responsible access are plentiful.
So, go forth and explore. Armed with knowledge, you will make wise choices. Stay curious, and stay connected. The internet's waiting for your skillful navigation!
HP Laptop WiFi Nightmare? Solved! (No Adapter Found Fix)Steal Your Neighbor's Wi-Fi: The Secret Laptop Download Trick!
Ah, the siren song of free Wi-Fi! Let's be honest, we've all been tempted. Picture this: you're staring at your laptop, craving that download fix, but the dreaded data limit looms. Or maybe you're just stuck in a Wi-Fi dead zone, feeling utterly disconnected. The neighbor's router, however, is chugging along, broadcasting a strong signal. That, my friends, is where the little devil on your shoulder whispers, "Just a peek…?" This isn't about preaching morality; it's about understanding the reality of the digital world. We're going to delve into the perceived possibility of leveraging your neighbor's Wi-Fi, not to condone it, but to understand the technical aspects and how these systems work. Think of it as a deep dive into the potential vulnerabilities of home networks, not a how-to guide for digital larceny.
1. The Allure of Free Bandwidth: Why We Even Think About It
Let's be real, the appeal is undeniable. Free internet equals savings. In a world where streaming services, online gaming, and hefty software updates gobble up data like Pac-Man, the idea of tapping into an unlimited source of bandwidth is, frankly, alluring. It's like stumbling upon a hidden buffet – you can't help but consider what's on the menu. Think of those movie nights, video calls with loved ones, or that late-night gaming session. All of it hinges on a stable, reliable internet connection. But what if that connection is financially out of reach? Or perhaps spotty and expensive where you are? We get it! The frustration! The temptation! But let's keep in mind the legality and ethics as we explore this fascinating (hypothetical) scenario.
2. The Digital Neighborhood Watch: Understanding Wi-Fi Security Basics
Before we even consider any digital exploration into our neighbor's network (and let's be clear, we're mostly just considering here), understanding Wi-Fi security is essential. Think of it like knowing the locks on your own front door before trying to pick someone else's.
- WEP (Wired Equivalent Privacy): An oldie but a goodie. Unfortunately, it’s as secure as a screen door on a submarine. Easily cracked.
- WPA/WPA2 (Wi-Fi Protected Access): A significant upgrade, offering much better security. Still, it's not Fort Knox.
- WPA3: The latest and greatest, offering the strongest protection. If your neighbor is using this, you’ve got a tougher challenge (hypothetically, of course).
The strength of the security depends on the password complexity and the type of encryption used.
3. Cracking The Code (Hypothetically): Common Weaknesses and Vulnerabilities
Okay, let's say, hypothetically, someone wanted to assess a Wi-Fi network. Where would they begin?
- Default Passwords: Many people don't change the default password on their router. This is like leaving your house keys under the doormat. Ridiculously easy to exploit.
- Weak Passwords: Simple passwords are easily cracked using brute-force attacks (trying every possible combination). Think of it as repeatedly punching the lock until it gives way.
- Wi-Fi Protected Setup (WPS): This feature, designed for easy setup, can sometimes be exploited. It's like a backdoor you didn't know existed.
- Social Engineering: Tricking your neighbor into revealing their password, which is a classic maneuver that requires absolutely no technical expertise. But very, very wrong.
Important Note: We are discussing these for informational purposes only. Attempting to access someone else's Wi-Fi without their permission is illegal and unethical.
4. The "Tools" of the Trade (Purely Hypothetical, of Course!)
If someone hypothetically wanted to investigate a network's vulnerability, what tools might they use? Again, let's stress, this is for educational purposes only.
- Network Scanners: Tools that identify devices connected to a network and gather information.
- Password Cracking Software: Programs that attempt to crack passwords through various methods.
- Packet Sniffers: These tools intercept network traffic, potentially revealing passwords or other sensitive data (purely hypothetical, of course).
Using these is like having a toolbox with all the wrong intent.
5. The Legality Labyrinth: What the Law Says About Wi-Fi Piracy
Stealing Wi-Fi is like stealing anything else: it's theft of service. In most jurisdictions, unauthorized access to a Wi-Fi network is illegal. You could face fines, lawsuits, or even criminal charges. So, yeah, not worth it. It's like trying to cross a minefield to get a better view.
6. The Ethics of the Equation: Is It Right?
Beyond the legality, there's the ethical dimension. It's about respecting your neighbor's property and privacy. Would you want someone snooping on your data? Think about your digital footprint and how it might affect others. Would you want your neighbor using your connection?
7. The Downside of Digital Trespassing: Potential Risks
Even if you hypothetically managed to access someone's Wi-Fi, you're opening yourself up to several risks.
- Legal Consequences: As we already discussed, this is not good.
- Security Risks: You could be blamed for the actions of any malicious actors who use the connection.
- Reputational Damage: Getting caught is never fun.
Think of it like walking on a tightrope – one wrong step, and you're in trouble.
8. Protecting Your Own Network: Strengthening Your Defenses
So, how do you prevent your Wi-Fi from being "borrowed"?
- Strong Passwords: Use a complex password with a mix of letters, numbers, and symbols.
- Enable WPA3: If your router and devices support it, make the upgrade.
- Change Your Default Password: Immediately!
- Keep Your Router Firmware Updated: Patches often fix security vulnerabilities.
- Disable WPS: It's a potential security risk.
- Monitor Your Network: Regularly check connected devices in your router settings.
Basically, lock the door.
9. Alternative Solutions: Exploring Legitimate Options
Instead of considering unauthorized access, explore legitimate options:
- Ask Your Neighbor: The simplest and most ethical solution! Some neighbors might be happy to share or offer a guest network.
- Public Wi-Fi: Libraries, coffee shops, and other public places often offer free Wi-Fi.
- Mobile Hotspot: Use your phone's data plan to create a hotspot.
- Upgrade Your Internet Plan: If possible, consider a plan that fits your needs and budget.
Like finding a shortcut on a map, there is often a better way to get where you want to go.
10. The "Guest Network" Gambit: A Safe Harbor?
If you do want to share your Wi-Fi, consider setting up a guest network. This isolates guests from your primary network, limiting their access to your personal devices and data. It is like building a separate room for your guests.
11. The Speed Factor: How Neighborly Wi-Fi Might Affect Your Experience
Even if you hypothetically gained access, the speed might be disappointing. If your neighbor is streaming 4K movies, your download speeds will crawl. It's like trying to share a single slice of pizza with everyone in the neighborhood. The original user's bandwidth is shared.
12. The Bandwidth Bandit: How Your Actions Affect Your Neighbor
Your activity on your neighbor's network could impact their experience too. If you're excessively downloading, they might notice slower internet speeds. It's like borrowing their car and emptying the gas tank.
13. The Moral Compass: When Curiosity Just Isn't Worth It
We are constantly reminded of the importance of ethical behavior, both online and offline. Is the potential benefit of a free connection worth the potential risks and ethical compromises? Think about it!
14. The Future of Wi-Fi Security: Staying Ahead of the Curve
As technology evolves, security measures will continue to improve. Staying informed about the latest threats and best practices is essential for protecting your own network (and avoiding any temptations to, shall we say, stretch the boundaries of network access). It is important to keep updated and informed.
15. The Real Download Trick: Finding the Right Solution
The real "download trick" isn't about stealing Wi-Fi; it's finding a solution that works for you – ethically, legally, and sustainably. Consider the options we've discussed, and make the best possible decision for your circumstances.
Closing Section
Ultimately, the allure of "stealing" Wi-Fi boils down to a desire for connectivity and cost savings. But the potential downsides – legal troubles, ethical breaches, and security risks – far outweigh the benefits. Instead of focusing on illicit methods, we encourage you to explore legitimate, sustainable solutions. Respect your neighbors, protect your own network, and embrace the digital world responsibly. Remember, the best download trick is the one that doesn't come at
Laptop WiFi AC KILLER: Get Blazing-Fast Speeds NOW!How to Install Any Laptop Wi-Fi Driver without Internet for Windows 1087
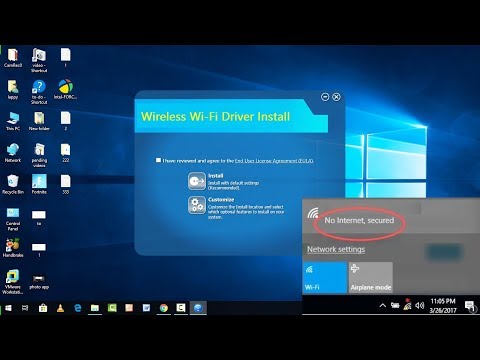
By MJ Tube How to Install Any Laptop Wi-Fi Driver without Internet for Windows 1087 by MJ Tube
Windows 10 - How To Install Wifi Drivers

By tech How Windows 10 - How To Install Wifi Drivers by tech How
Download your WIFI Drivers by doing this

By ADVANTI Download your WIFI Drivers by doing this by ADVANTI

Title: How to Install Any Wifi Drivers without Internet in Windows 11 PC or Laptop - 2025
Channel: Discover You
How to Install Any Wifi Drivers without Internet in Windows 11 PC or Laptop - 2025 by Discover You
My Laptop Work
Steal Your Neighbor's Wi-Fi: The Secret Laptop Download Trick? A Comprehensive Guide
The digital age thrives on connectivity. We rely on it for work, entertainment, and staying in touch with the world. However, the ever-present need for Wi-Fi can sometimes lead us to questionable solutions. While this article delves into the topic of accessing your neighbor's Wi-Fi, it's critically important to understand that unauthorized access to a private network is illegal and unethical. This guide is for informational purposes only and aims to educate on the technical aspects of Wi-Fi security, not to encourage or endorse any unlawful activities. We strongly advise against attempting to access a network without the explicit permission of the network owner.
Understanding Wi-Fi Security Protocols
Before considering any technical aspects, understanding the fundamental security protocols that safeguard Wi-Fi networks is crucial. These protocols are designed to prevent unauthorized access and protect the data transmitted over the airwaves.
WEP (Wired Equivalent Privacy): A Historic Weakness
WEP, the oldest protocol, provided a foundational layer of security. However, its weaknesses are well-documented. The 40-bit or 104-bit key lengths are easily crackable using readily available tools. WEP’s vulnerability stems from its flawed key generation and the way it handles initialization vectors (IVs), making it susceptible to brute-force attacks.
WPA/WPA2 (Wi-Fi Protected Access): A Significant Leap Forward
WPA and WPA2 represent a significant improvement over WEP. They utilize more robust encryption algorithms, such as TKIP (Temporal Key Integrity Protocol) and AES (Advanced Encryption Standard), and employ more substantial key lengths. WPA2, the later iteration, uses AES encryption exclusively, making it significantly more secure than WPA. However, even WPA2 has vulnerabilities, particularly when weak passwords are used.
WPA3: The Current Standard and Enhanced Protection
WPA3 is the latest and most secure standard. It incorporates enhanced encryption protocols, including Simultaneous Authentication of Equals (SAE), which eliminates the vulnerabilities of pre-shared key (PSK) authentication. This makes it much more difficult to crack passwords, even if a user has multiple attempts. WPA3 also provides better protection against brute-force attacks and offers individual data encryption, enhancing security on public Wi-Fi networks.
Legitimate Wi-Fi Discovery and Connection Methods
If you're looking for legitimate ways to connect to Wi-Fi, several options are available. These methods are entirely legal and ethical, ensuring you can access the internet without compromising your integrity.
Public Wi-Fi Hotspots: Availability and Security Considerations
Public Wi-Fi hotspots are prevalent in various locations. Restaurants, cafes, libraries, and airports offer free Wi-Fi access. However, it’s crucial to consider the security implications. Public networks often have less robust security, making them vulnerable to eavesdropping. Always use a VPN (Virtual Private Network) when connecting to these networks to encrypt your internet traffic. Also, consider the type of data you are transmitting. Refrain from sharing sensitive information, like your credit card details, on public networks.
Mobile Hotspots: Creating Your Own Network
Many smartphones and mobile devices allow you to create a mobile hotspot. This feature uses the device’s cellular data connection to share an internet connection with other devices. The advantage is the creation of a private, secure connection. The downside is the potential for significant data usage, depending on your cellular plan. Keep a watchful eye on your data consumption!
Guest Wi-Fi Networks: Sharing Access Safely
If you have a home Wi-Fi network, many routers allow you to create a guest Wi-Fi network. This separates the guest network from your primary network, allowing guests access to the internet without revealing your private data and settings. Guest networks typically have a separate password, allowing you to control access easily.
Technical Aspects of Wi-Fi Cracking (For Informational Purposes Only)
As previously stated, we strongly discourage any attempt to access an unauthorized Wi-Fi network. This section merely provides a theoretical overview of the methods that could be used and is meant to enhance the understanding of network security.
Wi-Fi Adapters: The Hardware Component
To attempt to access a Wi-Fi network without permission, you would need a Wi-Fi adapter capable of performing packet injection and monitor mode. Standard Wi-Fi adapters in laptops and desktops often do not have these capabilities. Specific adapters are designed for this purpose. These adapters are designed to be used to scan networks, capture data packets, and attempt to crack passwords.
AirCrack-ng: A Popular Network Cracking Suite
AirCrack-ng is a widely-used suite of tools for Wi-Fi security auditing. It can be used to capture Wi-Fi traffic, crack WEP and WPA/WPA2 passwords, and analyze network vulnerabilities. AirCrack-ng contains various tools for deauthentication attacks, which can be used to force wireless clients to reconnect, capturing the necessary handshake data.
Packet Sniffing: Capturing Network Traffic
Packet sniffing involves intercepting and analyzing network traffic. A network sniffer, also called a packet analyzer, is used to capture packets of data as they travel over a network. These packets contain various information, including passwords, usernames, and other sensitive data. Packet sniffing is used to identify security vulnerabilities and potential threats.
Password Cracking: Brute-Force and Dictionary Attacks
Once the handshake data is captured, a password-cracking program can be used to attempt to recover the network password. This is typically done through brute-force attacks (trying all possible password combinations) or dictionary attacks (using a pre-compiled list of common passwords). The success rate depends on the password's strength.
Ethical Considerations and Legal Ramifications
The ethical and legal implications of unauthorized Wi-Fi access are significant. Respecting the privacy and property of others is paramount.
The Importance of Consent
Accessing a Wi-Fi network without the explicit consent of the network owner is a violation of privacy. It is unethical to use someone else's resources without their permission. Always ask permission before attempting to connect to someone's network.
Consequences of Unlawful Access
Attempting to access a Wi-Fi network without authority carries substantial legal risks. Depending on the jurisdiction, unauthorized access can lead to criminal charges, including fines and imprisonment. There is also the potential for civil lawsuits.
Protecting Your Own Network: Best Practices
Securing your own Wi-Fi network can prevent others from attempting to gain unauthorized access.
Strong Passwords: The First Line of Defense
Use a strong, unique password. Employ a combination of uppercase and lowercase letters, numbers, and symbols to make it difficult for attackers to crack. Regularly update your password, especially if you suspect a security breach.
Enable WPA3 Encryption: The Latest Security Standard
If your router supports it, enable WPA3 encryption. This provides the most robust security. If your router is older and does not support WPA3, make sure your router uses WPA2.
Router Firmware Updates: Security Patches
Regularly update your router’s firmware. These updates often include security patches to address known vulnerabilities. Keep your router updated.
Network Segmentation: Create a Guest Network
As mentioned earlier, create a guest network to isolate guest devices from your primary network. This minimizes the risk of unauthorized access to your sensitive data.
Monitoring Network Activity: Identifying Suspicious Behavior
Monitor your network activity for suspicious behavior. Review your router’s logs to identify any unauthorized devices or unusual traffic patterns. This can alert you to potential security breaches.
